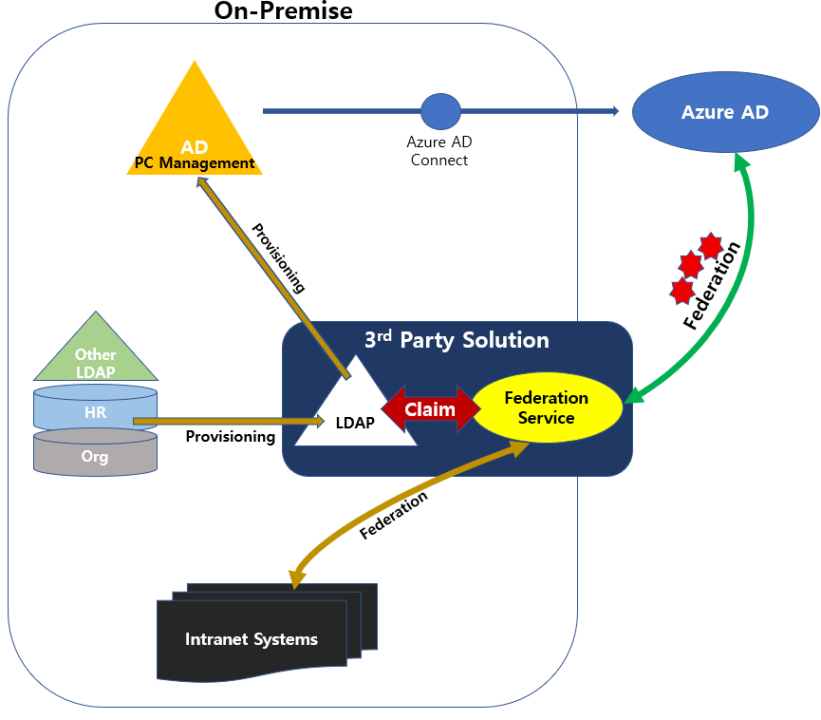
Integrating Active Directory (AD) with third-party authentication services is a common practice to enhance security and simplify user management across multiple platforms. When measuring security in such an integration, several factors need to be considered. Here are some steps, an example, and tools to help you measure security in this scenario:
- Risk Assessment: Start by performing a comprehensive risk assessment to identify potential security threats, vulnerabilities, and potential impacts of integrating AD with third-party authentication services.
- Authentication Protocols: Ensure that the third-party authentication service supports secure authentication protocols like OAuth 2.0, OpenID Connect, or SAML (Security Assertion Markup Language).
- Encryption: Check if the communication between the third-party authentication service and Active Directory is encrypted using SSL/TLS to protect data in transit.
- Multi-Factor Authentication (MFA): Consider implementing MFA to add an extra layer of security to the authentication process. This could involve using a combination of passwords, biometrics, or one-time passwords (OTP).
- Authorization and Access Control: Define clear access control policies, ensuring that users have appropriate permissions within both AD and the third-party service.
- Logging and Monitoring: Implement comprehensive logging and monitoring mechanisms to detect and respond to potential security incidents effectively.
- Compliance and Standards: Ensure that the integration complies with relevant security standards and regulations based on your organization's requirements.
- Vendor Assessment: If you are using a third-party authentication service, conduct a vendor assessment to evaluate their security practices and certifications.
- Penetration Testing: Perform regular penetration testing to identify and address any security vulnerabilities.
Let's consider an example of integrating Microsoft Azure Active Directory (Azure AD) with a third-party application that requires user authentication.
Suppose your organization is using a cloud-based project management tool, and you want to allow users to log in using their Azure AD credentials. The third-party application supports OAuth 2.0 for authentication.
- Microsoft Azure Active Directory: The primary tool for managing user identities and access in Azure.
- OAuth 2.0 Playground: A helpful tool to test OAuth 2.0 authentication flows and ensure they are configured correctly.
- Security Assertion Markup Language (SAML) Tracer (Browser Extension): This tool allows you to monitor and inspect SAML messages exchanged during the authentication process, helping you identify potential issues.
- Security Information and Event Management (SIEM) Solution: A SIEM solution, such as Splunk or ELK Stack, can be used for logging and monitoring security-related events during the integration process.
- Vulnerability Scanning Tools: Various vulnerability scanners, such as Nessus or OpenVAS, can be utilized to identify potential security flaws in the integration.
Remember that the choice of tools may vary based on the specific requirements of your integration and the technologies involved.
In conclusion, when integrating Active Directory with third-party authentication services, it's crucial to assess risks, implement appropriate security measures, and use relevant tools to ensure a secure and reliable authentication experience for your users. Regular security audits and updates are essential to maintain a high level of security in this integration.